April Email Scam Roundup – ASIC, MyGov, eWAY & MYOB
Scam Emails Targeting Australian Businesses
We will take a look at some of the most recent email scams targeting Australian businesses from April 2017. Share this list with your colleagues to spread awareness of recent scams which may come across your email inbox.
April was another strong month for email scams with new variations showing up and interesting methods of attack.
To verify, report or learn more about a scam contact the ATO Scam Report or ScamWatch.
My Gov
With more than 11 million accounts or roughly 50% of the population, the Australian government online portal is a prime target for scammers trying to imitate government departments holding sensitive information. A legitimate looking email sent from no-reply@mygov.net has caused many raised eyebrows after recipients were advised to verify their identity using the link contained in the email.
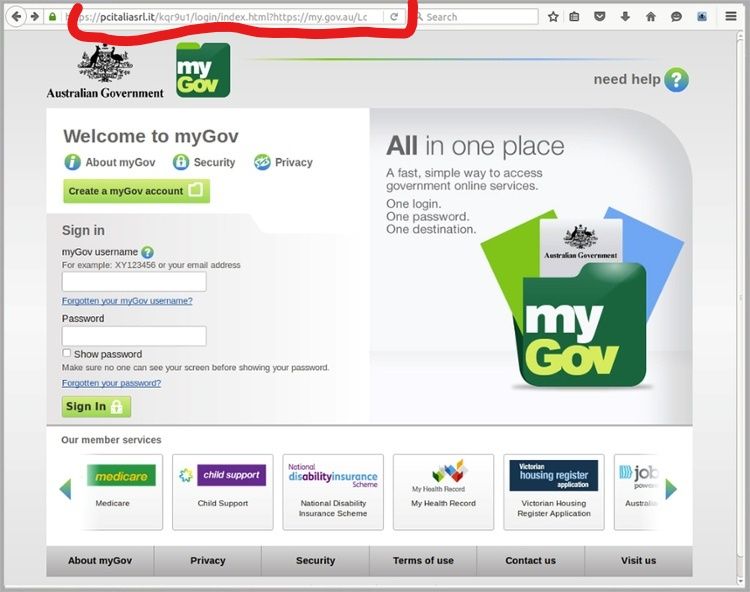
Victims who clicked the link were directed to the above fake website intended to dupe recipients into sharing their password and credit card information. The only indicator of the fraudulent nature of the site is the unusual URL which is not an Australian Government domain. According to Mailguard, upon further inspection the source code for the authentic government website has been directly copied for the above clone.
After inputting their username and password the victim is prompted to confirm credit card information as can be seen below.
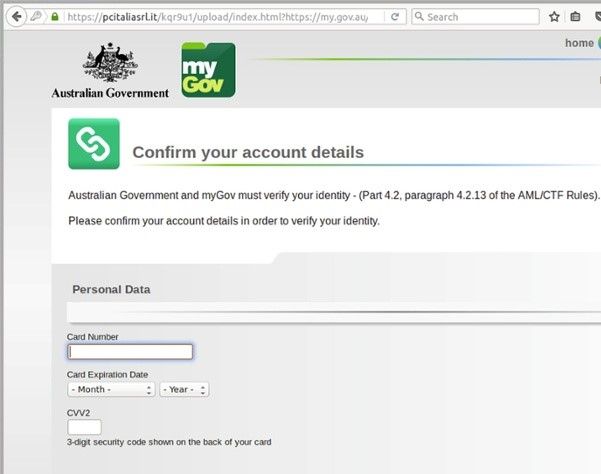
After providing credit card information the victim is redirected to the real My Gov website in order to confuse and attempt to validate the email request. According to MailGuard, the email originated from servers hosted in the Czech Republic, which are likely to have been compromised. The sending address used is noreply@mygov.net, which has no relationship with the legitimate portal

Cyber Insurance Can Help Reduce Costs Following Email Scams.
ASIC
The Australian Securities and Investments Commission is always popping up in these lists of scams due to the nature of their work. In this email scam business owners are sent a well branded, legitimate reading email regarding the renewal of their company. With complete ASIC logo, wording and legitimate links to the ASIC privacy policy the unsuspecting business owner can easily mistake this email for official communication. Especially if received around the correct date before their official ASIC renewal.
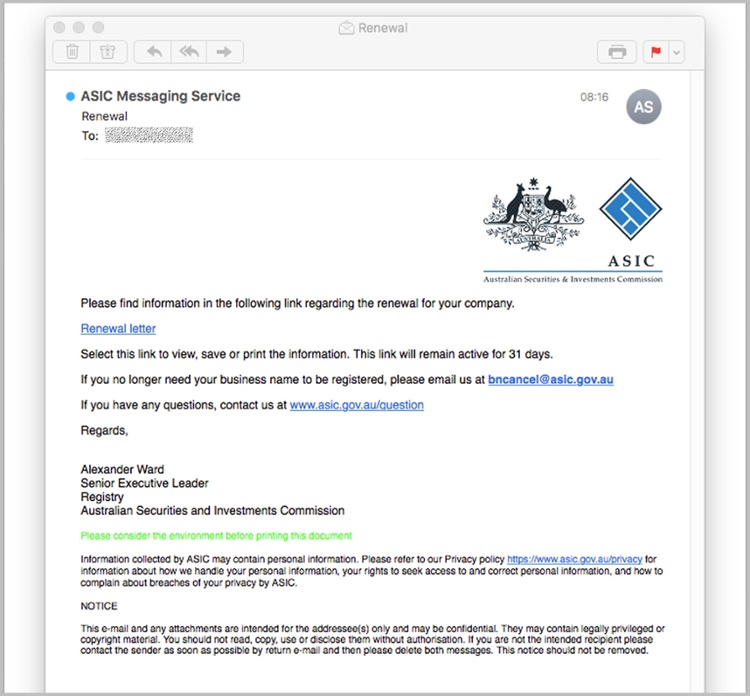
Victims are prompted to follow a link to find their renewal letter, instead the link contains java script code designed to install malicious software on their computer systems. The software is then likely to download additional ransomware or a trojan causing business interruptions and unforeseen costs for victims. The email was sent from a newly created austgov.com domain, instead of the legitimate ASIC site, asic.gov.au. The fake domain which was registered in China has experts speculating that due to Chinese registration laws, it is likely that a stolen ID was used to create the domain which raises further questions about the people behind these scams.
MYOB
Thousands of fake MYOB emails have begun making their way to inboxes across Australia. The well branded email appears to be a legitimate invoice from a company using the MYOB software package. As is common with these email scams, additional links to the real website are included in the fine print of the email to add validity. The link to the invoice however will direct victims to a compromised SharePoint website containing a malicious file.
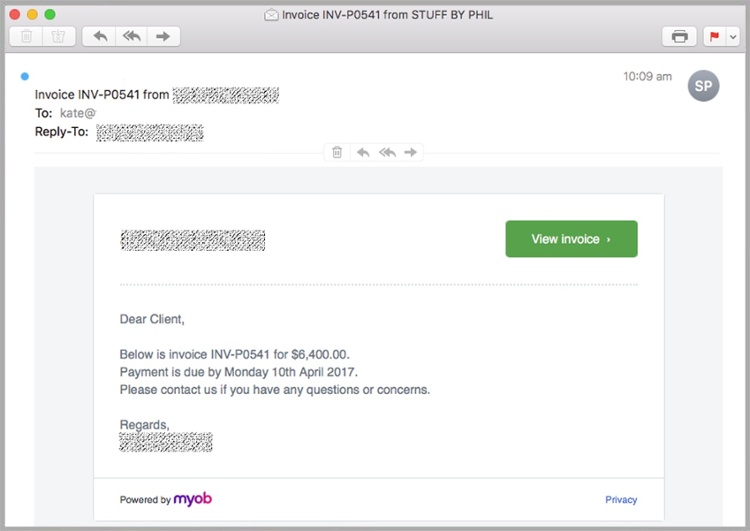
Similar to the above ASIC scam and many in the past, the emails were sent from a fake, newly-registered domain myob-australia.com. Many variations of the email wording and company info have been observed from many recipients, which indicates the culprits are attempting to obscure their red flags from antivirus software.
Once the victim’s curiosity gets the best of them and they follow the link, the malicious software will install itself to automatically run when the machine is switched on in an attempt to capture private information from internet browsers.
eWAY
Online payment company eWAY has had their corporate identity imitated in a bulk run of scam emails which targeted Australians with macros capable of downloading malicious software.
The fake emails were sent from a recently registered domain, estoreway.info, instead of the legitimate Australia-based site, eway.com.au. The emails not only came from an incorrect domain which is quickly verified using google, unusual grammar is also a clear sign throughout the text.
A screenshot of the email scam courtesy of Mailguard seen below advises recipients their recent purchase has been approved and will be shipped to the address in the attached invoice.
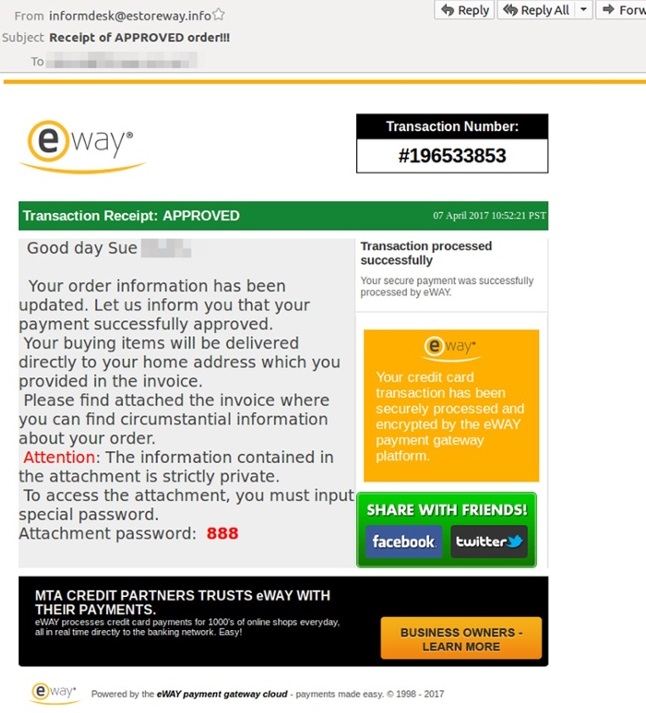
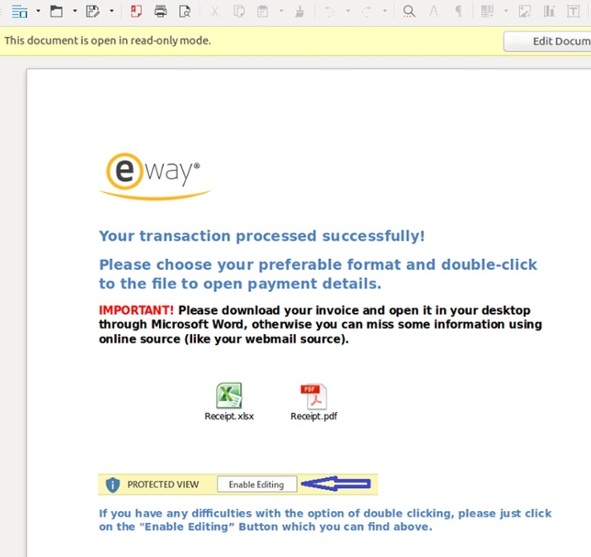
The attached invoice contains a Word document with a malware downloader within. The attachment is capable of downloading and executing malicious software to record and gather sensitive information. In an additional attempt for the scammers to establish legitimacy the attachment requires a password to unlock and view the ‘invoice’. Once victims click on the attachment they will receive instructions to “Enable Editing” which essentially opens the door for criminals to begin automatically installing malicious files.

Cyber Insurance Can Help Reduce Costs Following Email Scams.
That is our April list of malicious emails to keep a look out for, feel free to comment with any malicious emails we missed. Each month we will be updating and reporting new malicious emails making the rounds for Australian businesses.
Subscribe and follow Cyber Insurance Australia on Linkedin & Facebook for regular updates and information. Thanks to MailGuard , subscribe to the security blog for regular updates here.
To ensure email security for your business, contact DDM Security Systems to learn more about email encryption & protection.
Share this list with your colleagues to help spread the word before one of these nefarious emails ends up at your business.
The ASIC website offers the following advice for avoiding email scams:
- Keep your antivirus software up to date
- Be wary of emails that don’t address you by name or misspell your details and have unknown attachments
- Don’t click any links on a suspicious email.
Above all we recommend educating employees to recognise suspicious emails and unusual behavior without curiosity getting the best of them.


Comments
Not found any comments yet.