5 malicious emails to be aware of!
Malicious Emails Continue to Compromise
Here is our January 2017 wrap-up of large scale malicious emails making the rounds for Australian businesses.
We have all received some suspicious emails in the past and laughed at the seemingly obvious red flags, it appears that gone are the days of the poorly translated foreign prince simply trying to return your unknown wealth. Today, as employee education continues to increase, criminals are very fastidious and clever with their malicious email phishing attempts.
To verify or report a scam contact the ATO Scam Report or ScamWatch.
Australia Post
Earlier this month a torrent of Australia Post scam emails were discovered with a simple method of infection designed to evade anti-virus software. At the time of discovery by MailGuard, only 1 of 68 popular antivirus vendors were detecting the link as malicious
The message indicates a parcel is ready for collection at their local post office, simply confirm your correct postal address by clicking the link at the bottom of the email.
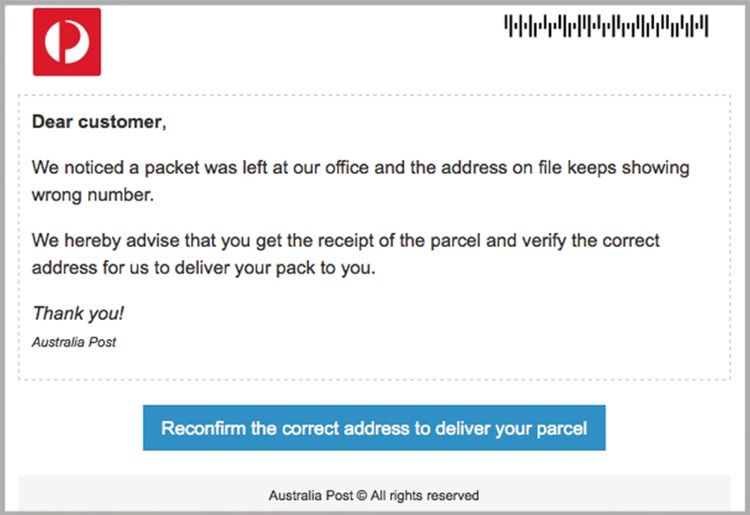
Malicious Australia Post Email
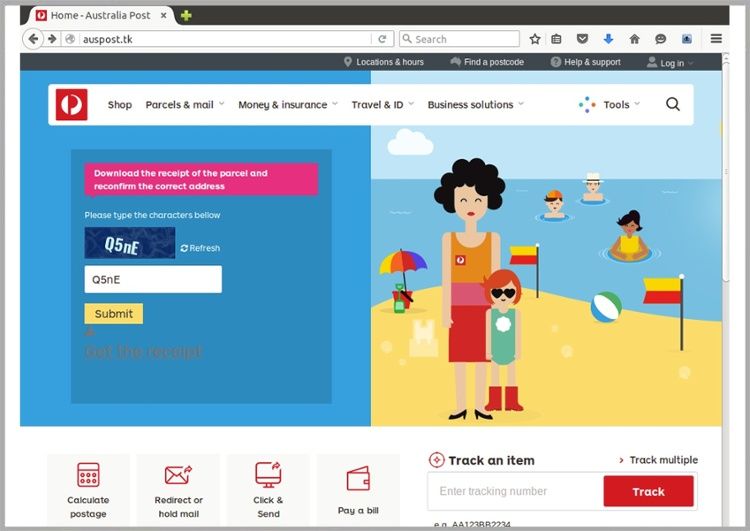
Replica Australia Post Website
After clicking to confirm, a series of prompts leading to an identical Australia Post website end with a remotely executed malicious file being downloaded. An identical Australia post website has been created with the noticeable difference being the www.auspost.tk address instead of the official www.auspost.com.au, the malicious website even has ‘Captcha’ security forms and correctly scales for mobile users.
Help protect your business with cyber insurance.
Australian Securities and Investments Commission – ASIC
Reports of fake emails claiming to be from ASIC are making the rounds and distributing malware at an alarming rate. “Malware can reformat your hard drive, alter, delete or encrypt files, steal sensitive information, send unauthorised emails, or takes control of your computer and all of the software on it.”
“The message claims to contain an important message. But those who click to the link inadvertently download a malicious JavaScript file. The file is housed within a zip file on a compromised SharePoint site.” said Jaclyn McRae of Mailguard.
The emails have been disguised using a third party program which causes them to appear to be sent from a legitimate @asic.gov.au account.
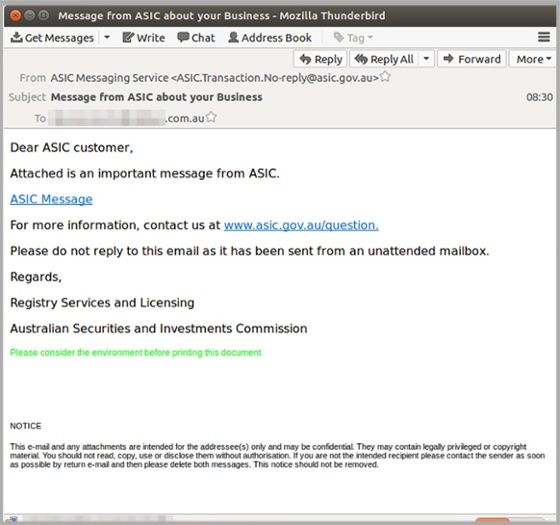
ASIC email scam
According to MailGuard, at the time of reporting, none of 68 well-known antivirus vendors were detecting the link as malicious.
“Scammers pretending to be from ASIC have been contacting Registry customers asking them to pay fees and give personal information to renew their business or company name,” “These emails often have a link that provides an invoice with fake payment details or infects your computer with malware if you click the link.”ASIC says.
Australian Taxation Office – ATO
The next government organisation being impersonated is the Australian Tax Office. The malicious emails are coming from a recently registered set of domains with slight variations to the correct ATO web address which is https://www.ato.gov.au.
“The email looks quite legitimate, and includes the recipient address within the text body. It includes Australian Government branding and confidentiality clause.”said Jaclyn McRae
The email contains a Microsoft Word attachment which the recipient is told requires their attention.
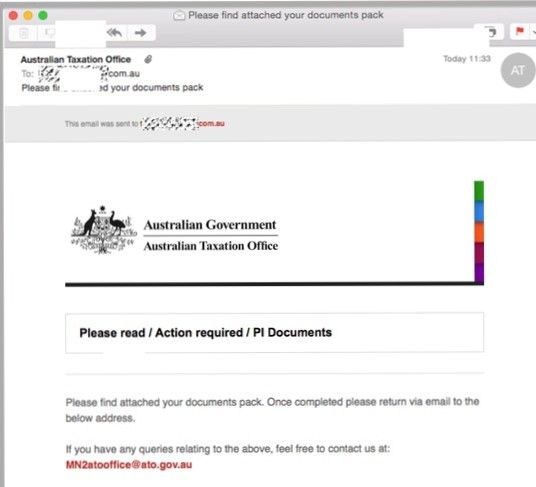
ATO scam email
“The attached document contains a a macro which when executed, downloads a virus from a remote location.”
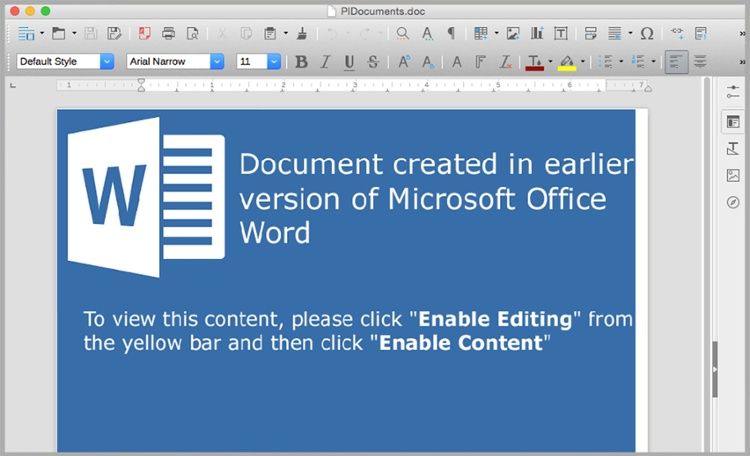
Microsoft Word Malicious Macro
We’ve recently written about malicious Microsoft Office macros and other methods of infection, here.
“Adversaries are increasingly using Microsoft Office macros – small programs executed by Microsoft Office applications such as Microsoft Word, Excel or PowerPoint – to circumvent security controls that prevent users from running untrusted applications. Microsoft Office macros can contain malicious code resulting in a targeted cyber intrusion yielding unauthorised access to sensitive information.”
Commonwealth Bank
Apart from government departments, financial services giants are also regular targets. ANZ, Macquarie and AMEX have been recent targets of phishing scams.
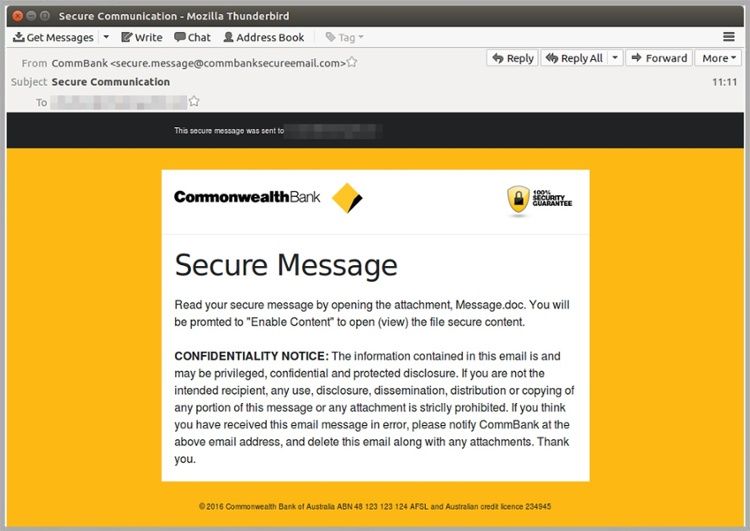
Commonwealth Bank scam email
Very similar to the above mentioned ATO email scam, Commonwealth Bank customers have been sent the above secure message requiring the attached content to be downloaded. Once again, the Microsoft Macro contained in the Message.doc attachment downloads a virus from a remote location. Once recipients ‘enable editing’ and then ‘ enable content’ the virus is activated.
According to the MailGuard Security Blog , the malicious emails were sent from cloud-hosted servers in Hong Kong but the attack could have originated anywhere.
Driving Infringement Notices
A round of malicious emails poorly disguised as driving infringement notices has been targeting Australians for a few months. The continued attempts from criminals suggests some measure of success.
Despite having no branding, the ‘from’ name having no relationship to the sending domain and no reference to which police authority had issued the fine, it seems many targets have taken the bait.
According to MailGuard, “The malicious emails claim the recipient has incurred a fine for negligent driving. It says the fine will arrive in the mail, but that it can be viewed by clicking the link.”
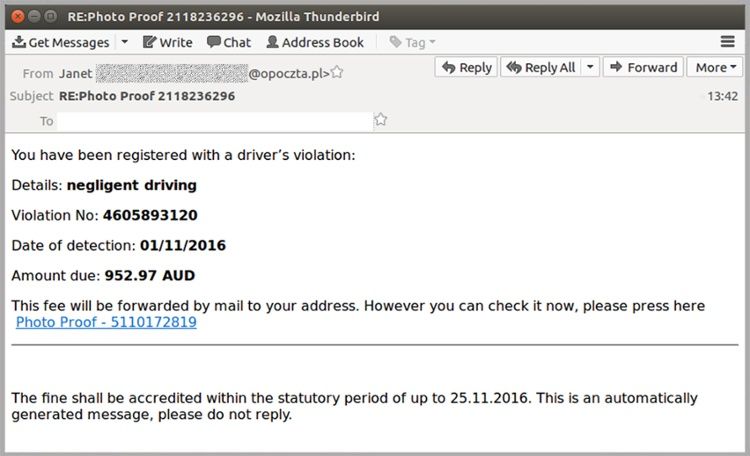
Negligent driving scam email
The “photo proof” attachment contains a link which accesses a malicious ZIP archive and allows malicious software to be downloaded.
Conclusion
Thanks to MailGuard, subscribe to the security blog for regular updates here.
Each month we will try to highlight some common email scams targeted at the Australian market.
If we have missed a scam you think is important, please let us know below.


Comments
Not found any comments yet.