
September Email Scam Roundup – Telstra, ASIC, Xero & more
Another month and another list of email scams being targeted at Australian business owners, let’s dive in and take a look at a few of the nefarious, clever and also simple ways criminals are attacking Aussies. September has been a big month despite major media coverage lacking after the previous Petya & Wannacry attacks.
Each day millions of malicious emails are sent to individuals and business owners with ever increasing sophistication. The scammers responsible for the below scams are part of well organised and funded criminal groups which put increasing amounts of effort into their activities.
For perspective, the 2013 Europol Serious & Organized Threat Assessment reported that cyber crime is now more profitable than the global drug trade.
To verify, report or learn more about a scam contact ScamWatch.
Throughout September, Telstra has been impersonated multiple times from different scammers trying to leverage the telecommunication giants reputation and email billing system. As can be seen in the first image below, scammers have duplicated the Telstra email bill format, wording and branding from authentic bills in an attempt to increase legitimacy. Typically these scams advise that an outstanding amount is overdue and to follow the provided links for immediate payment. This scam however notifies many recipients that their account is actually in credit and is relying on the curiosity of victims to click without looking for suspicious warning signs.
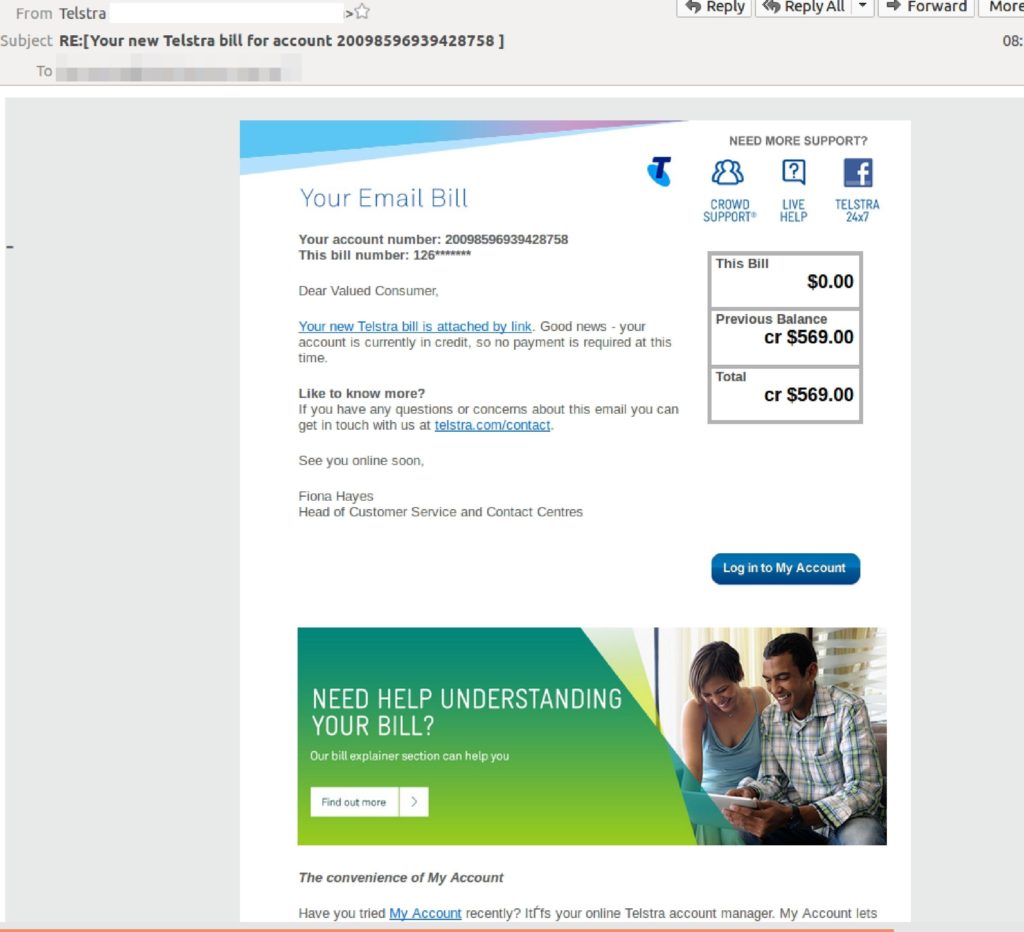
The above email link initiates a malicious file download which is designed to steal sensitive information. In this instance scammers are using randomised account numbers, we recommend checking for warning signs such as sending address and a lack of personalisation. Official Telstra bills will have account holder information and personalisation.
A similar Telstra email scam made the rounds this month, not as sophisticated as the above duplicated email but just as malicious. As seen below, the email contains very few errors and ironically contains official links to other pages such as the Telstra email fraud page warning about exactly these emails.
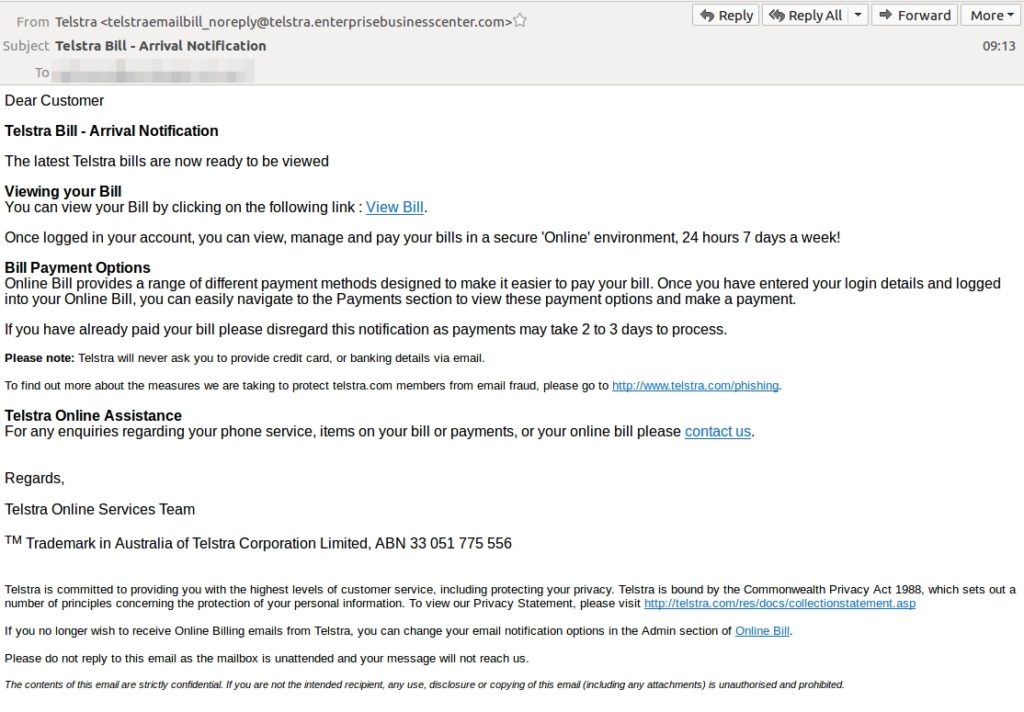
Despite it’s lack of branding, many Australians were thrown by the well worded format and very close sending address to the official Telstra email bill address.
Xero
The below Xero email courtesy of Mailguard shows a very convincing Xero invoice which has been sent to Australian businesses. The email presents a PDF containing the invoice details in a very similar fashion to the official Xero emails. This scam relies on randomised amounts from random business names to intrigue recipients into checking the invoice.
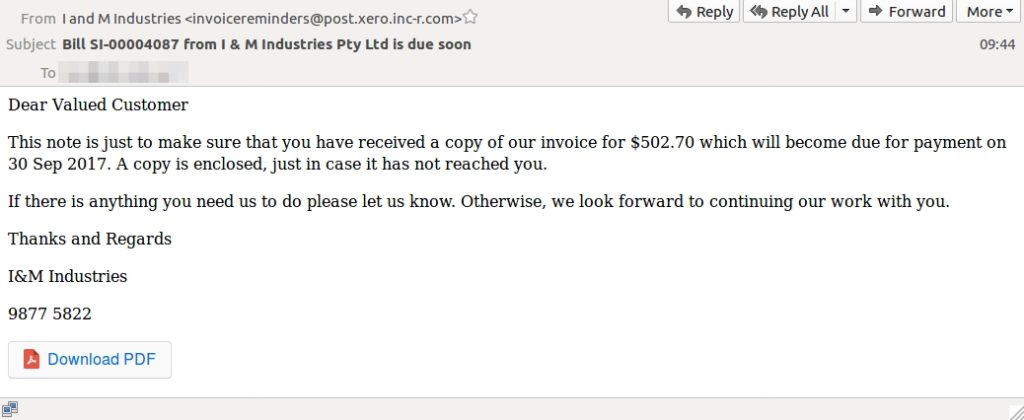
The PDF is not an attachment but instead a link to download malware onto the recipients machine. The sending address appears to be legitimate at first glance but quickly you’ll notice the unusual ending of “@ post.xero.inc-r.com”, a good reminder to always check the sending address.
AusPost has been impersonated in the past but this particular scam uses Microsft OneDrive branding for the emails. The malware arrives as “AusPost Service Notification” with a randomised subject line similar to ‘AusPost Track – 123456789 -100-98765 Monday September’. Recipients are prompted to view the delivery details in OneDrive using the link provided.
Once clicked, the link takes recipients to a random web page where they are urged to download a .zip file containing malicious software designed to encrypt their information in exchange for a bitcoin ransom. According to the Australian Government, identical scam emails have also been seen impersonating the Australian Federal Police and e-Toll.
ASIC
Similar to previous ASIC scams we have written about in July, April and May. The government department was once again the victim of a large run of malicious emails from cyber criminals looking to impersonate the ASIC brand and reputation.
A sample email seen below shows how well duplicated this attempt is. The spelling and grammar has very few mistakes, they have used legitimate branding lifted from official documents and included links to the official privacy policy and ASIC help section. The two main red flags are the sending address , asic.transaction. no-reply@ ato.gov.autsl.com which according to Mailguard was registered 24 hours prior in China and the lack of individual personalisation.
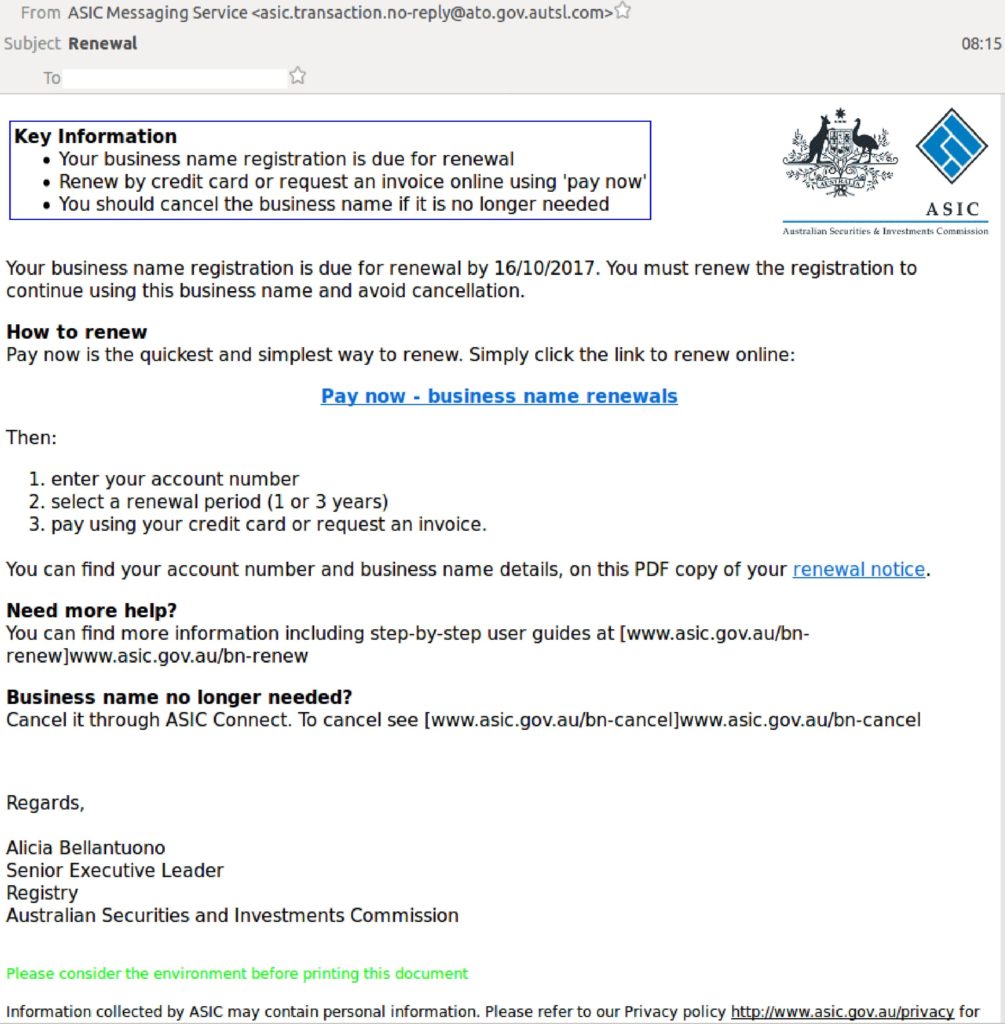
Recipients are prompted to click a link to download their renewal notice. The link presents a suspicious .zip archive to download which contains malicious files designed to steal personal information. Look out for suspicious ASIC emails as they are a never ending target of impersonation by cyber criminals.

This was a small sample of the malicious emails which arrive in inboxes every day. Many scams operate in a similar fashion but use different brands for legitimacy, we will continue to report scams each month in an attempt to help raise awareness. Thanks to MailGuard for their regular blog updates on scam emails circulating in Australia.
In the event that your business is impacted by a cyber attack, data breach or email scam, cyber insurance is a cost effective way to mitigate the expenses, reputational damage and financial loss.
Subscribe to the newsletter and follow Cyber Insurance Australia on Linkedin & Facebook for regular updates and information.

Comments
Not found any comments yet.