June Email Scam Roundup – Origin, MYOB, & Petya
Email Scams & Global Ransomware Attacks
Each month Cyber Insurance Australia takes a look at some of the email scams being targeted at Australian business owners. June has been a big month in the news with the Petya ransomware attacks getting major media coverage around the world and across Australia after our beloved Cadbury chocolate factory fell victim.
Each day around the world millions of malicious emails are sent to individuals and business owners with ever increasing sophistication. The scammers responsible for the below scams are part of well organised and funded criminal groups which put increasing amounts of effort into duping as many people as possible.
According to MailGuard, ” Cybercriminals have been inundating Australians with fraud emails this month, with the number of large-scale scam email attacks as high in one day as an average week.”
To verify, report or learn more about a scam contact the ATO Scam Report or ScamWatch.
NSW Roads & Maritime Services
Yet another government department has been impersonated in a large scale email scam this month. Over the past few months we have written about scams being targeted at ASIC , MYGOV and the ATO. This month Australians received an email from the NSW Roads & Maritime Services department regarding an E-Toll account statement. The email which can be seen below shows a well copied email template which uses the official Roads & maritime branding, logo and privacy statement.
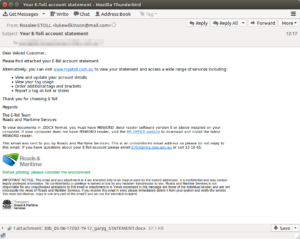
The email directs recipients to view the attached statement which contains malicious software. This email scam doesn’t address recipients by name, hold any personal information or indicate an overdue toll amount, it simply relies on the curiosity of people to open anything from an authoritative source. Malware is designed to interrupt, destroy, gain control of or steal data from a computer system.
This definitely won’t be the last time a government department is impersonated for email scams.
EnergyAustralia
EnergyAustralia was also impersonated this month with fake invoices being sent with randomised amounts due within a matter of days. Cyber criminals will randomly generate an amount for the invoice in an attempt to avoid detection from security software. The email seen below shows a well duplicated and legitimate looking email from EnergyAustralia.
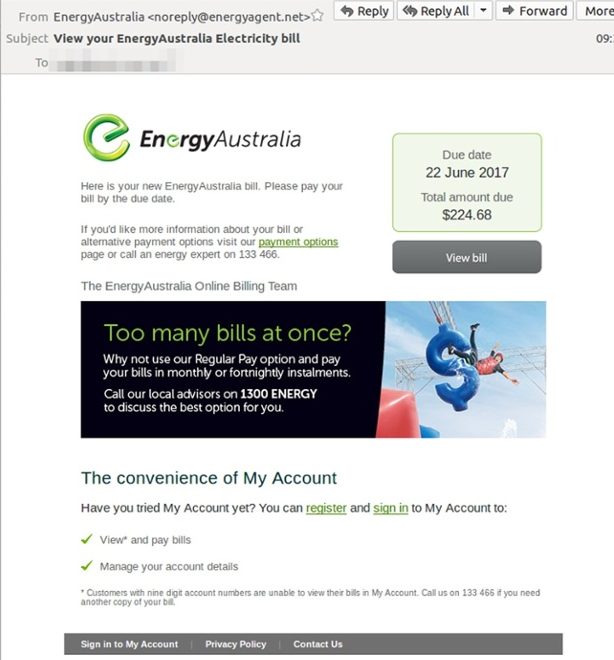
The email scam was sent from “noreply@ energyagent.net”, a domain recently registered in china. The email contains a “View bill” link which downloads a nefarious “EnergyAustralia Electricity bill.zip” file containing malware. Always check small details such as the sending address when receiving suspicious emails.
If you have received this email, you can report it to EnergyAustralia by forwarding the email to staysafe@energyaustralia.com.au. Please send the hoax email as an attachment if possible. Don’t forward the hoax email to anyone else.
Once you’ve sent the hoax email to staysafe@energyaustralia.com.au, delete it from your inbox immediately. Then empty your Deleted Items folder.
EnergyAustralia’s advice regarding email scams from their website.
MYOB
In the lead up to End of Financial Year criminals are targeting businesses using the popular accounting software package MYOB. Criminals are using the MYOB brand in their email scams for added legitimacy. The emails indicate an attached invoice for a random amount of money which was due in April 2017. The business names used in the email scam are unrelated and are added to help deceive their recipients.
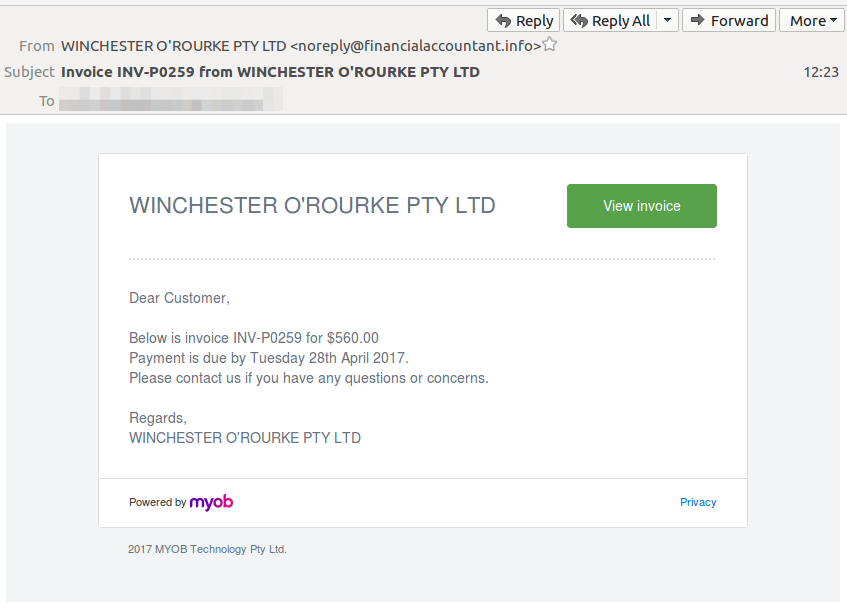
According to MailGuard, the “view invoice” button links to a .ZIP file which contains malware. This type of malware can steal private information from internet browsers, automatically run the malicious software at windows startup and more.
MYOB is no stranger to impersonation tactics from cyber criminals, many email scams rely on large brands which businesses have a high chance of working with to catch unsuspecting victims.
Origin Energy
Origin are a regular target for email scams as a large number of their customers receive email correspondence and Origin provide services for such a high percentage of Australians. Origin have had their brand impersonated numerous times in the past, the continued use of their branding and other energy providers indicates the efficacy of this type of scam. The most recent Origin email scam comes just days after Origin officially announced price increases via email which added to confusion for recipients.
The below email was sent from the recently registered domain, noreply@ globalenergyfinance.com, instead of an official Origin address.
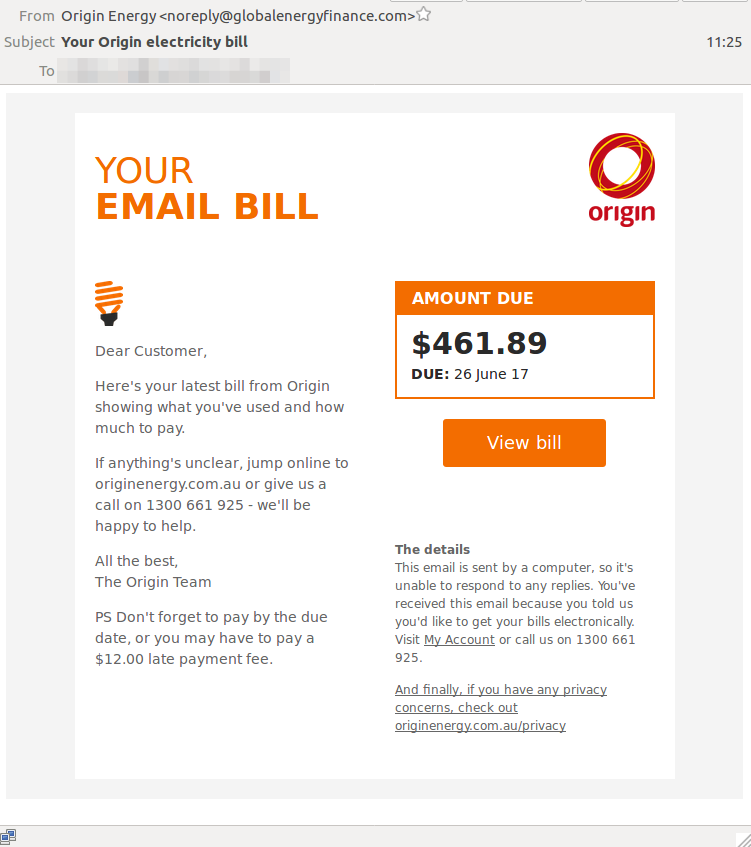
In the past, these email scams were often noticeable due to the poor wording used and lack of legitimate logos, branding and contact details. The above Origin scam which MailGuard estimates was sent to approximately a quarter of Australian businesses is clearly well written and shows an increasing level of sophistication.
Very similar to the above approaches, when recipients click the “View bill” button a download is prompted which contains a malicious file named “Origin electricity bill.js”. The malware in this scam is similar to the above MYOB malware which can
- steal private information
- Install itself for autorun at Windows startup
- Implement a process that significantly delays the analysis task
Origin Energy recommends seeking advice from www.scamwatch.gov.au or www.staysmartonline.gov.au if you think you’ve been scammed.
Petya Ransomware
Last month the media reported on the global “WannaCry” outbreak but June saw “Petya” take the spotlight. Similar to other forms of ransomware, the basic principle is to interrupt and lock the victims computer operations while demanding a ransom paid in bitcoin. The amount demanded for Petya appeared to be $300USD and infected hundreds of thousands of computers. Many victims around the world are left scrambling including Russia’s biggest oil company, Ukrainian banks and multinational shipping and advertising firms.
The Tasmanian Cadbury chocolate factory had production halted when the computer systems were attacked. “It’s a highly advanced site and highly automated. Most of the production process is controlled by computers,” said John Short of the Australian Manufacturing Workers’ Union regarding the Cadbury factory.
In a statement, Cadbury’s parent company Mondelz International said they “do not know when our systems will be restored” and “We continue to work quickly to address the current global IT outage across Mondelz International,”.
Below is a screenshot of what victims are faced with after infection.
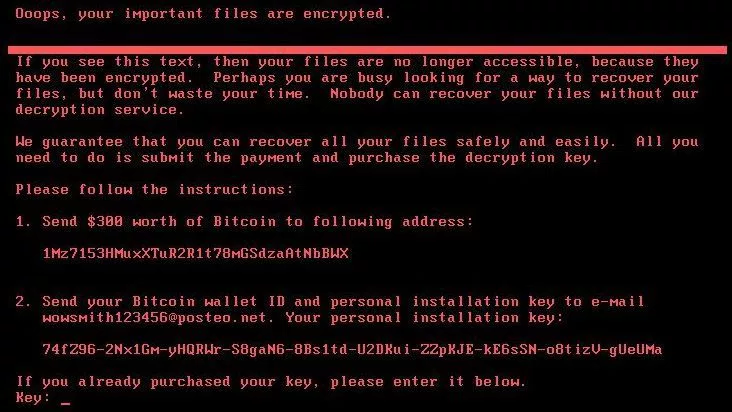
“It’s like the NSA built a kind of digital Ebola, used it secretly for five years, and now it’s out in the wild. #Petya” – Nicholas Thompson, Editor in Chief, Wired.
Stay Smart Online has released the following information regarding the Petya ransomware and what businesses can do:
There are very simple steps you can take to reduce the risk of your personal and business records being impacted by Petya ransomware. The top two steps are:
- Immediately install the latest Windows updates for applications, software and operating systems. Note that updates are also available for Windows XP.
- Confirm that backups are available and working – guidance on backups is available for businesses and individuals and households.

Cyber Insurance Australia can help reduce the costs of cyber crime for your business.
Each month we will be updating and reporting new malicious emails making the rounds for Australian businesses.
Subscribe and follow Cyber Insurance Australia on Linkedin & Facebook for regular updates and information. Thanks to MailGuard , subscribe to the security blog for regular updates here.
Share this list with your colleagues to help spread the word before one of these nefarious emails ends up at your business.