What is Ransomware?
More than 48% of small to medium victims paying up
Ransomware, like any sort of malware, can get into your organisation in many different ways: most often buried inside email attachments, via poisoned websites, through exploit kits, on infected USB devices and occasionally even as part of a self-spreading network worm.
Receiving spam emails is part and parcel of doing business for a large number of Australian and international businesses. Regularly our staff speak with staff who laugh “of course” when asked if they receive suspicious emails from unsolicited addresses. The overwhelming awareness is increasing but the seriousness is still lacking as some employees scoff at the sophistication of these emails. We’ve written previously about recent malicious emails making the rounds and their complexity which has caught many Australians off guard.
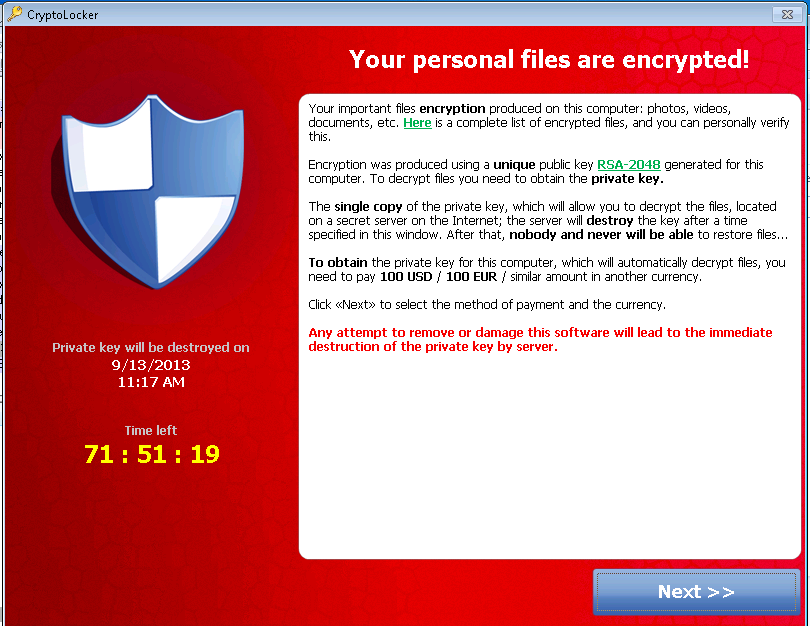
What is Ransomware?
Ransomware can encrypt the files on a computer (including network file shares and attached external storage devices), prevent you from accessing windows or stop certain apps from running, victims are then directed to a webpage with instructions on how to pay a ransom in bitcoin to unlock the files. The ransom has typically ranged from $500 – $3000 in bitcoin. Microsoft have seen some recent ransomware make you complete surveys which give micro payments to the criminal for each finished survey.
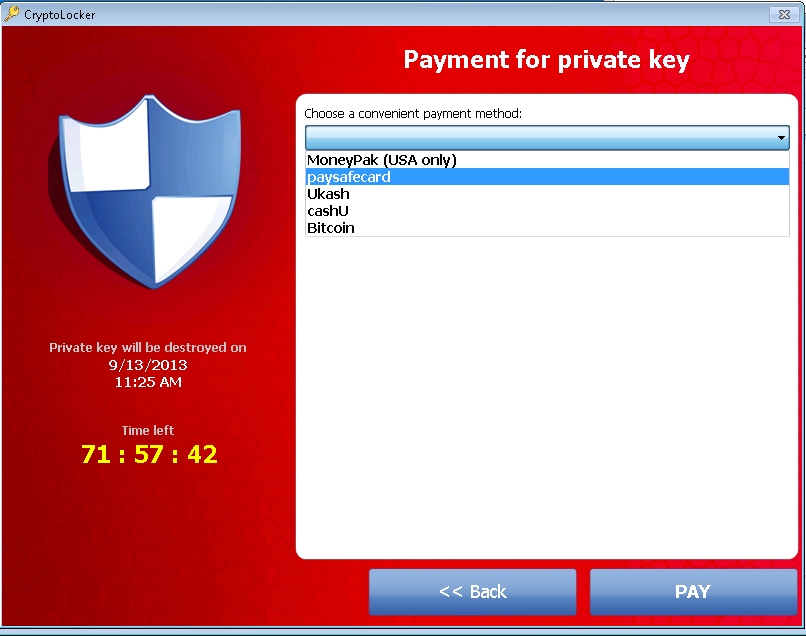
There are different types of ransomware. However, all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC. Usually, the attackers specifically research and target a victim (similar to whale-phishing or spear-phishing – and these in fact may be techniques used to gain access to the network). They can target any PC users, whether it’s a home computer, endpoints in an enterprise network, or servers used by a government agency or healthcare provider.
Protect your business with cyber insurance.
Ransomware By The Numbers
A recent survey in the U.S indicated that more than 50% of small to medium enterprise (SME) have experienced ransomware and of those, a staggering 48% have paid the ransom.
Reports in 2016 that more than $1 billion was taken in from ransomware alone with an even higher figure expected for 2017. “The $1 billion number isn’t at all unreasonable and might even be low,” confirmed Mark Nunnikhoven, vice president of cloud research at Trend Micro. The amount of money up for grabs is incredible and it is easy to see why potential cyber criminals are enticed and existing criminal groups have switched their methods.
The above figure was gathered by monitoring known criminal bitcoin wallets. More than $50 million was tracked for each of three wallets associated with the Locky ransomware, and a fourth one that processed close to $70 million. Cryptowall brought in close to $100 million before it was shut down this year. CryptXXX gathered in $73 million during the second half of 2016, and Cerber took in $54 million.
Smaller ransomware families brought in another $150 million, and the FBI has reported $209 million in ransomware payments during the first three months of 2016. In addition to this $800 million or so in known payments, there are many other Bitcoin wallets that are unknown to researchers and uncounted, pushing the estimated total to $1 billion for all of 2016.
A Mimecast survey in 2016 found that 34 percent of Australian executives consider ransomware to be a ‘high threat’ – well ahead of the 25 percent in the US and 18 percent in South Africa.
Time frames for ransom payments can range from as short as 48 hours to as long as 1 week.
Over 4,000 ransomware attacks occurred daily since January 1,2016 which is a 300% increase on the 1,000 daily attacks recorded in 2015 according to the US Department of Justice.
Preemptive Protection
Employee Education
Employee error is the number one reason for the majority of data breaches and cyber intrusion events. Having a good information security culture for all staff is beginning to take hold as directors are being shown that this isn’t simply an IT issue.
Data Protection Services
Arranging a solid data protection solution is a terrific fail-safe. As important as employee education is, the same goes for the information security procedure in place on a daily basis. There is a myriad of data protection solutions on the market today from numerous vendors for all aspects of the digital side of business. Have your business audited today!
A couple of recommended Australian options are DDM Security Systems, MailGuard and Asterisk Information Security.
Up to date software & patches
Applying patches and other software fixes as soon as they become available is one of the best ways to keep criminals away from your sensitive information. Software manufacturers regularly update versions to include newly found software vulnerabilities that attackers could otherwise exploit. While staying up to date will not stop all attacks, it can make the process more difficult and potentially discourage attackers from accessing to your system.
Most recent versions of popular software can be configured to download and automatically update, giving you a great start toward keeping your business secure online.

Protect your business with cyber insurance.
The majority of businesses we have spoken with unfortunately only took precautions as a reactive measure following a breach. Staying ahead of the curve and taking steps to put comprehensive cyber security measures in place before it’s too late is still the strongest option.
More resources and information about what a typical attack looks like and it’s life cycle can be found here.

