2016 Cyber Security Report released
The Australian Cyber Security Centre has released the 2016 threat report.
The ACSC is an important Australian Government initiative which brings together existing cyber security capabilities across Defence, the Attorney-General’s Department, Australian Security Intelligence Organisation, Australian Federal Police and Australian Crime Commission.
Each year the government departments release their collective data for an eye opening report about national, commercial and private online security.
Between July 2015 and June 2016, CERT Australia responded to 14,804 cyber security incidents affecting Australian businesses, 418 of which involved systems of national interest (SNI) and critical infrastructure (CI). The incidents affecting SNI and CI are broken down by sector below.
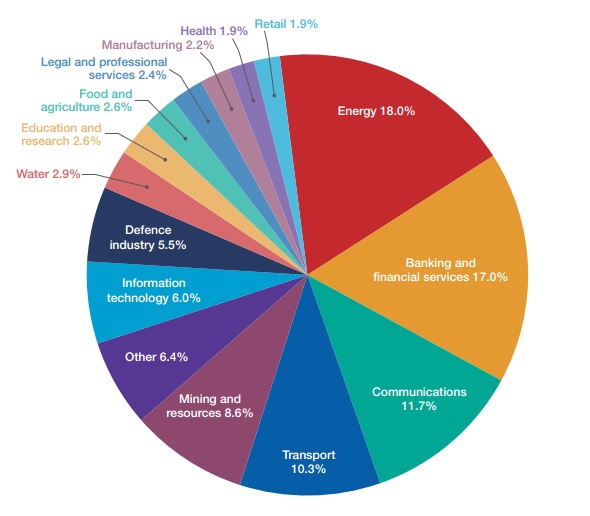
As CERT Australia relies on the voluntary self-reporting of information security incidents from private, commercial and government sources throughout Australia and internationally, CERT is unfortunately not able to get a complete view of all incidents. A large number of businesses which have been victims of a breach have paid a bitcoin ransom or fixed their system without notifying CERT or their cyber insurance provider.
According to CERT, the energy and communications sectors had the highest number of compromised systems. The banking and financial services and communications sectors had the highest number or DDoS attacks while the highest number of malicious emails was received by the energy and mining sectors.
Insure your business against cyber crime.
Trending exploitation techniques
- Spear Phishing – emails containing a malicious link or file attachment with methods used becoming more convincing and difficult to spot. As such, spear phishing emails continue to be a common exploitation technique used in the compromise of Australian industry networks.
- Ransomware – Ransomware encrypts the files on a computer (including network fileshares and attached external storage devices) then directs the victim to a webpage with instructions on how to pay a ransom in bitcoin to unlock the files. The ransom has typically ranged from $500 – $3000 in bitcoins.
- Web-seeding techniques – By compromising web sites frequently visited by targets, adversaries are able to exploit targets without overt communication, such as spear phishing emails. Strategic web compromises have proven effective for thematic campaigns, such as targeting foreign policy and defence organisations via the compromise of think tanks and media organisations, but pose an equal threat to all users.
- Malicious advertising – “Malvertising” allows an adversary to target a specific audience by exploiting online advertisement networks used by popular websites that visitors trust. Typically, either malicious code is inserted into an ad being presented to users in the course of their normal browsing or a benign ad is used to redirect the user to somewhere that will download malicious code automatically.
- Microsoft office macros – Adversaries are increasingly using Microsoft Office macros – small programs executed by Microsoft Office applications such as Microsoft Word, Excel or PowerPoint – to circumvent security controls that prevent users from running untrusted applications. Microsoft Office macros can contain malicious code resulting in a targeted cyber intrusion yielding unauthorised access to sensitive information.
- DDoS extortion – A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. DDoS extortion occurs when a cyber adversary threatens to launch DDoS activities against an organisation unless a fee is paid.
- Secondary Targeting – There has been an increase in the detection of cyber adversaries attempting to gain access to enabling targets – targets of seemingly limited value but which share a trust relationship with a higher value target organisation. It is imperative that organisations understand that they might be targeted solely based on their connections with other organisations – the real target of these adversaries.
- Targeted Disclosures – While the theft and targeted disclosures of sensitive information is not a new threat, the employment of the tactic in such a brazen manner against high profile entities has almost certainly lowered the threshold of adversaries seeking to conduct such acts.
- Credential Harvesting Campaigns – emails direct the user to access a document via Google Drive, and by clicking on a “View Document” link, the user is then directed to a webpage where credentials are requested and thereby harvested by the adversary. Emails are then sent from the compromised user’s account to contacts contained in the compromised user’s address book, meaning the malicious emails will appear to be coming from legitimate and trusted sources.
What does a typical cyber security compromise look like?
Intial foothold
The attacker sends a spear phishing email with a malicious link to their target which when opened will execute malware creating an entry into the network.
Network Reconnaissance
After access has been granted the attacker will continually monitor and study the network, search for domain administration credentials and possibly propagate through other linked networks. As an example, an adversary will regularly access the network to gain updated user credentials, thus avoiding losing access because of password changes.
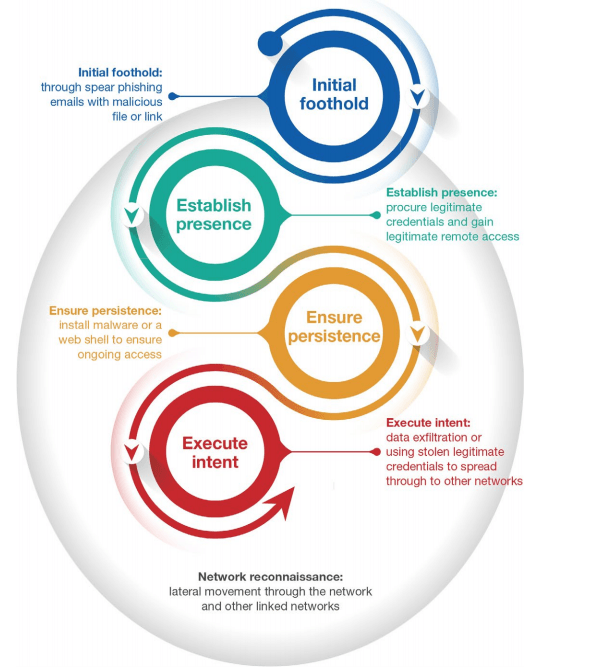
Establish Presence
Once in the network, adversaries will attempt to obtain legitimate user credentials with the goal of gaining legitimate remote administrative access. After legitimate credentials are obtained, the adversary will transition from malware dependant tradecraft to the use of Virtual Private Network (VPN), Virtual Desktop Infrastructure (VDI), or other corporate remote-access solutions combined with software native to the organisation.
Ensure Persistence
Adversaries strive to install malware or a web shell to ensure ongoing access should their legitimate accesses cease to function. Malware is typically configured with a limited “beacon rate” to minimise network traffic and evade network defenders. However, web shells are increasingly being used as they generate zero network traffic and are difficult to detect unless the adversary is actively interacting with them.
Execute Intent
Once persistent access is gained, the adversary will execute their intent. This intent could be anything from data exfiltration to enabling lateral movement to the real targeted organisation, exploiting circle of trust relationships between the organisations.
Insure your business against cyber crime.
Further Resources
Mitigation of Targeted Cyber Security Intrusions
The mitigation strategies tailor and provide additional controls that make the mitigation strategies relevant to current and emerging issues such as ransomware and other destructive malware, malicious insiders, and industrial control systems.More information can be found at http://www.asd.gov.au/infosec/mitigationstrategies.htm
The Australian Government Information Security Manual (ISM)
The Australian Government Information Security Manual (ISM) assists in the protection of official government information that is processed, stored or communicated by Australian government systems, and is available at http://www.asd.gov.au/infosec/ism/index.htm
CERT Australia (Computer Emergency Response Team)
CERT Australia’s public website contains useful information for Australian businesses in relation to mitigating cyber security incidents and security issues affecting major Australian businesses. More information can be found at: https://www.cert.gov.au/


